Canonical
on 10 August 2017
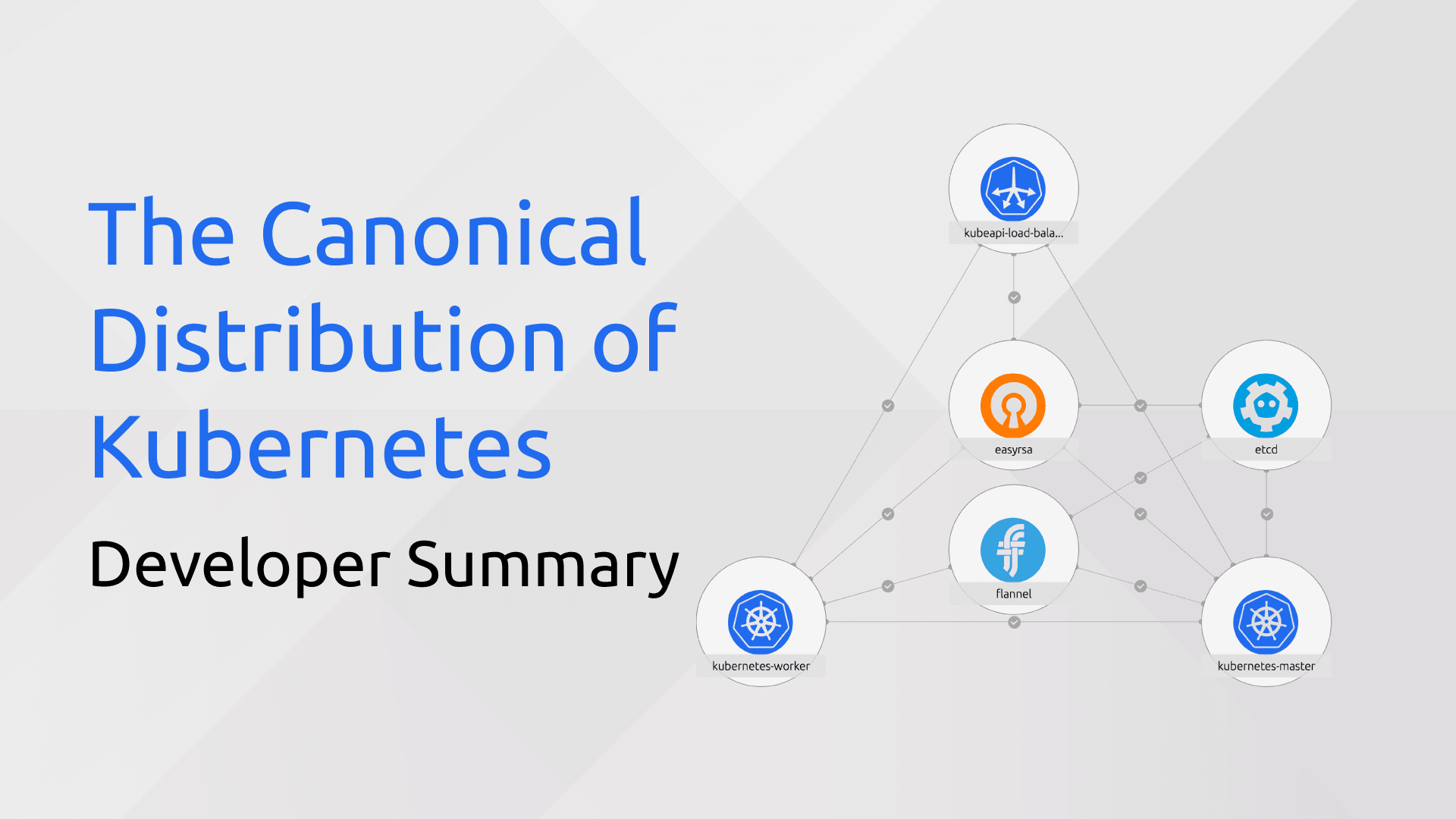
August 4th concluded our most recent development sprint on the Canonical Distribution of Kubernetes (CDK). Here are some highlights:
Testing & Planning
- CDK offline testing plan. We wrote up a plan for testing CDK in an environment where there is no (or severely limited) egress internet access. The end goal is to ensure that CDK can be deployed in this scenario, and create docs describing how to do it. Initial testing begins in the current sprint.
- etcd2-to-etcd3 migration plan. We wrote up a plan for upgrading existing CDK clusters from etcd2 to etcd3 if desired, and making etcd3 the new default. While the plan is in place, we don’t have any implementation work planned in the current sprint.
- Canal. We wrote up a design doc for implementing Canal (Calico-on-Flannel) for CDK. Implementation of the Canal charm was scheduled for the current sprint and is currently in code review.
- We added a Jenkins job to test our stable charms against the latest upstream patch release. A passing build here tells us that we can release the latest binaries for CDK without breaking currently-deployed clusters.
Features
- Completed RBAC proof-of-concept work. At this point we know how to turn RBAC on/off via charm config, and what changes are needed in CDK to make this work. In the coming weeks we’ll be working on moving from proof-of-concept to production-ready.
- s390x support. We started by snapping the major cluster components. There are some docker images that don’t have s390x builds, namely nginx-ingress-controller, heapster-grafana, and addon-resizer. We’ll be following up on these in the current sprint.
- Calico. We updated the Calico CNI charm to use the latest Calico binaries, and added the Calico charm and bundles to CI.
If you’d like to follow along more closely with CDK development, you can do so in the following places:
- https://github.com/kubernetes/kubernetes (cluster/juju directory)
- https://github.com/juju-solutions/bundle-canonical-kubernetes
- Kubernetes Slack channels and SIG meetings
- #juju on Freenode IRC
- [email protected] mailing list
Until next time!
This was originally featured on Tim Van Steenburgh’s blog



